- Subscribe to RSS Feed
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Adtran Support Community
- :
- Documentation
- :
- Enterprise-Class Wi-Fi
- :
- Elite On-Premises
- :
- Configuring Unified User Access
Configuring Unified User Access
Configuring Unified User Access
- Introduction to Unified User Access
- Hardware and Software Requirements
- Deployment Concerns and Considerations
- Configuring Unified User Access
- Configuration Verification
- Troubleshooting
- Useful Links
Introduction to Unified User Access
This configuration guide will aid in the setup of Unified User Access in both vWLAN and Netvanta products running the Adtran Operating System (AOS).
The unified user access control software for vWLAN enables the control of users entering the network from wired ports and other manufacturers’ access points. This allows an enterprise to create a truly unified wireless and wired network by providing uniform service delivery, a seamless user experience, and consistent authentication irrespective of a user’s access method. The unified user access control software also simplifies administration by allowing all users to be addressed with the same set of policies.
Unified user access control is also an ideal solution for transitioning an existing wireless infrastructure to an Adtran Bluesocket wireless environment. It allows incremental wireless implementation with Adtran Bluesocket Access Points (BSAP) by leveraging existing third-party access points while providing the same user experience for all wireless clients.
Unified User Access Software is sometimes referred to as wired support, and this terminology may be be used throughout this documentation in place of unified user access software. Also, the term "wired client" may be used to describe both clients with a physical connection to the network and clients connecting to third-party access points.
Hardware and Software Requirements and Limitations
Unified User Access Software for vWLAN (part number 1951910G1) requires that each BSAP intended to support wired clients has the appropriate license. The part number shown previously can be used to obtain the required license. Previously licensed BSAPs may be re-provisioned for wired support simply by adding the new license. For new APs, these licenses come from the reseller or distributor. For replacement APs, the licenses will come from ADTRAN Customer Care when an RMA is processed.
Wired support relies on the use of virtual LANs (VLAN) to isolate wired client traffic. Any Netvanta product with 802.1q support can be used for Unified User Access. The AOS Feature Matrix - Product Feature Matrix will list products with VLAN Support (802.1Q). AOS products are not required for wired support, however, this guide does use these devices for example purposes. The use of AOS products also allows for greater compatibility as well as easier diagnostics should there be a need to contact Adtran Technical Support.
Deployment Concerns and Considerations
General knowledge of vWLAN is required in order to configure wired support. This guide will describe the various configuration areas surrounding wired support, but will not cover authentication mechanisms such as the Captive Portal which may be required for client connectivity. The Useful Links section will help locate the current vWLAN Administration Guide if needed.
Each BSAP with the appropriate license will support 32 clients from a source other than a BSAP. However, the BSAPs have a single Ethernet port, and all wired clients' traffic must flow into and out off this port in a hairpin fashion. This is combined with any wireless client traffic. A BSAP can be overwhelmed if proper care is not taken to balance the load of client traffic between multiple BSAPs. Only one BSAP can service an untrusted VLAN at any given time. Multiple BSAPs can be configured to support the same Access Group, but the vWLAN will decide which BSAP to use for wired support in the untrusted VLAN.
Wired support requires virtual LANs and 802.1q support. A basic understanding of 802.1q encapsulation (trunking) may be necessary to understand the ideas behind wired support, however, it is not required for this guide. The BSAPs use VLAN 1 for NAC addressing, and therefore VLAN 1 cannot be tagged on the BSAP's port. Further, the native (untagged) VLAN cannot be used as an untrusted VLAN. Depending on the expected number of wired clients, multiple untrusted VLANs may be required. This requirement is due to the fact that only a single BSAP can service a particular untrusted VLAN at any given time.
Configuring Unified User Access
There are two parts to configuring unified user access: the switching infrastructure and vWLAN. The vWLAN aspect is rather lite compared to the switching infrastructure. This requires uploading licenses, configuring access groups, and updating the AP templates. All AP template changes must be pushed to the BSAPs.
Wired support uses VLANs to help force client traffic through the BSAP. Wired client traffic flows into the BSAP through an untrusted VLAN, where the traffic is authenticated and policed (at layer 2). The traffic then flows out of the BSAP, as standard wireless traffic would, through a trusted (either tagged or native) VLAN. The BSAP will effectively bridge the wired clients' traffic into the trusted LAN, thus removing the need for any layer 3 interfaces in the untrusted VLAN. Because VLANs restrict broadcast traffic from being seen by devices in other VLANs, the BSAP will respond to important layer 2 traffic such as ARP and some DHCP messages. The client will believe it is the trusted LAN, however, it will send all of its traffic to the BSAP as if the BSAP were the gateway for the client.
One typical use case for wired support is library terminals. Library patrons could have the option to bring their own device for wireless use, but for those patrons who do not have a wireless device, the library can still provide wired terminals. The patrons using the terminals should still need to go through the same authentication methods as wireless clients. The examples presented below will use VLAN 100 for standard wireless clients (trusted VLAN), and VLAN 200 will be used for wired clients (untrusted VLAN). Keeping the library scenario in mind, and remembering that up to 32 wired clients will supported per licensed BSAP, a 48-port switch will be used for this example. In this way, a single switch can be used for all the wired terminals as well as additional BSAPs for wired and wireless support.
The switching infrastructure should be configured prior to configuring vWLAN. AOS devices can be configured using the web GUI or the CLI. Additional information is available within the Support Community if assistance is needed when Accessing the Command Line Interface in AOS.
The following requirements must be met within the switching infrastructure.
- At least one "untrusted" VLAN must be created for wired clients.
- The switchports connecting the BSAPs to the network must be configured to support 802.1q.
The following sections will assist in meeting these requirements when using Netvanta products running AOS.
AOS Configuration via the web GUI
Wired support relies heavily upon the use of VLANs to keep wired client traffic isolated. VLANs, by definition, will segment broadcast traffic such as ARP requests and DHCP Discover messages. This is needed to ensure the untrusted wired client traffic is processed through the BSAP. Using the left-hand menu of the AOS web UI (GUI), navigate to Data> Switch> VLANs. This screen will show all currently configured VLANs as shown in figure 2.
Figure 2. AOS GUI General VLAN Configuration
In figure 2, the wireless and wired VLANs have already been configured as VLAN 100 and VLAN 200 respectively, but there is one very important setting that must be pointed out for the wired VLAN. As stated previously, it is important that untrusted wired client is processed through the BSAP. This is aided by the absence of layer 3 interfaces in the VLAN, and therefore it is important that the VLAN is NOT configured as a VLAN Interface. Figure 3 demonstrates the correct setting in the VLAN configuration; the VLAN Interface option is not checked. Make sure the VLAN is Enabled, provide a descriptive name, and choose a VLAN tag. After applying the changes to the VLAN, the general VLAN configuration screen should reflect the new settings. A VLAN for Wireless clients should also be created at this time if one does not already exist. The options for the Wireless VLAN are not as strict as those for the Wired Client VLAN.
Figure 3. AOS GUI VLAN Configuration
Now the switchports can be configured to utilize these VLANs. Any wired clients with physical connections should be plugged into switchports configured as access ports on VLAN 200. In this example, a 48-port switch is being used. The following switchports will be configured as follows.
- Giga-swx 1/0/1 through giga-swx 1/0/32 will be used for wired clients.
- Giga-swx 1/0/33 is where the BSAP will be connected.
- Giga-swx 1/0/48 will be used as the uplink port to the rest of the network.
- All other ports will not be used for this example.
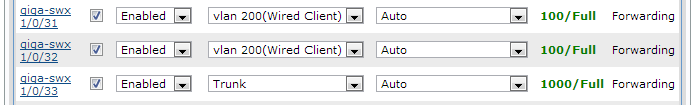
The switchports are configured by using the left-hand menu to navigate to Data> Switch> Ports. Use the drop-down menu to select which ports will be used as access ports (non-802.1q) and trunk ports (802.1q). Figure 4 shows the port configurations giga-swx 1/0/31-32 as well as giga-swx 1/0/33.
Figure 4. AOS GUI Switchport Configuration
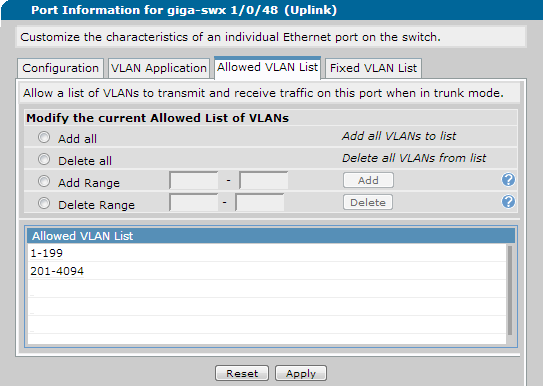
Giga-swx 1/0/33 and giga-swx 1/0/48 will be configured as a trunk port, but there is an additional configuration option on the uplink port 1/0/48. Isolating the untrusted VLAN 200 to this switch will be helpful in ensuring that wired support functions properly. The VLAN 200 traffic should not be allowed across the Uplink to the rest of the network. In the AOS web UI this is done by configuring allowed VLAN ranges. VLAN 200 needs to be excluded; this is accomplished by allowing VLANS 1-199 and 201-4094. The lower and upper bounds are limits set in AOS, so this setup will allow all VLANs except VLAN 200.
Figure 5. Uplink Port Configuration
Now that the switch configuration is complete, vWLAN can be configured.
Additional information is available within the Support Community to assist with Accessing the Command Line Interface in AOS. All configurations will start from the global configuration prompt. Access this prompt using the following commands.
> enable
Password: <input password>
# configure terminal
Wired support relies heavily upon the use of VLANs to keep wired client traffic segmented and isolated. VLANs, by definition, will segment broadcast traffic such as ARP requests and DHCP Discover messages. This is needed to ensure the untrusted wired client traffic is processed through the BSAP. Limiting layer 3 interfaces in the untrusted VLAN is essential to proper functionality within wired support. For this reason, VLAN 200 will be configured strictly as a VLAN and NOT an interface VLAN.
(config)# vlan 200
(config-vlan 200)# name "Wired Client VLAN"
(config-vlan 200)# exit
The 48 switchports will be configured as follows.
- Giga-swx 1/0/1 through giga-swx 1/0/32 will be used for wired clients.
- Giga-swx 1/0/33 is where the BSAP will be connected.
- Giga-swx 1/0/48 will be used as the uplink port to the rest of the network.
- All other ports will not be used for this example.
It is possible to configure a range of ports. Giga-swx 1/0/1-32 are going to be used for wired clients. These ports need to be configured as standard access ports in VLAN 200.
(config)# interface range gigabit-switchport 1/0/1-32
(config-swx 1/0/1-32)# switchport mode access
(config-swx 1/0/1-32)# switchport access vlan 200
(config-swx 1/0/1-32)# exit
Giga-swx 1/0/33 and giga-swx 1/0/48 will be configured as a trunk port, but there is an additional configuration option on the uplink port 1/0/48. Isolating the untrusted VLAN 200 to this switch will be helpful in ensuring that wired support functions properly. The VLAN 200 traffic should not be allowed across the Uplink to the rest of the network.
(config)# interface gigabit-switchport 1/0/33
(config-swx 1/0/33)# switchport mode trunk
(config-swx 1/0/33)# exit
(config)# interface port 1/0/48
(config-swx 1/0/48)# switchport mode trunk
(config-swx 1/0/48)# switchport trunk allowed vlan except 200
(config-swx 1/0/48)# end
The end command should bring the CLI session back to the enable prompt. Use the write command to save the configuration. A sample of the example configuration is provided below. Gigaswx 1/0/1-30 will be be configured the same as Giga-swx 1/0/31. Now that the switch configuration is complete, vWLAN can be configured.
!
interface gigabit-switchport 1/0/31
description Wired Client
no shutdown
switchport access vlan 200
!
interface gigabit-switchport 1/0/32
description Wired Client
no shutdown
switchport access vlan 200
!
!
interface gigabit-switchport 1/0/33
description BSAP
no shutdown
switchport mode trunk
!
!
interface gigabit-switchport 1/0/48
description Uplink
no shutdown
switchport mode trunk
switchport trunk allowed vlan 1-199,201-4094
!
Before provisioning any BSAPs for wired support, it is best to upload the licenses to vWLAN. Licenses are uploaded by clicking the Upload AP Licenses button on the Configuration> Wireless> AP Licenses screen (see figure 6). Each BSAP must be assigned to a domain, and the license upload screen will have a drop-down menu (as shown in figure 7) where the domain can be selected. After the licenses have been uploaded, the licensed BSAPs should show the correct information in the Wired License column as shown in figure 6.
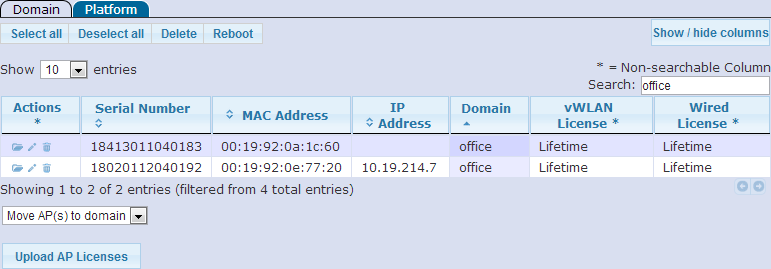 | 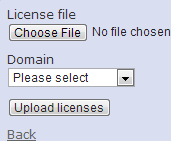 |
| Figure 6. vWLAN AP Licenses | Figure 7. License Upload Screen in vWLAN |
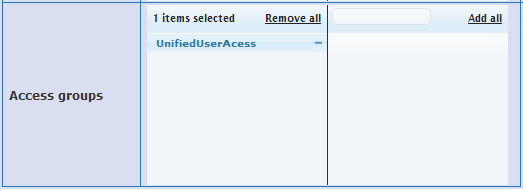
Once the BSAPs are licensed, the Wired Access Groups need to be configured. Wired clients will look like wireless clients to vWLAN, however, these clients do not connect to an SSID configured on vWLAN. Instead, wired clients connect to an untrusted VLAN. The Access Groups provide a list of untrusted VLANs and other security attributes. Wired Access Groups are shown and created on the Configuration> Wired> Access Groups screen as seen in figure 8. Clicking Create Access Group will bring up the screen shown in figure 9.
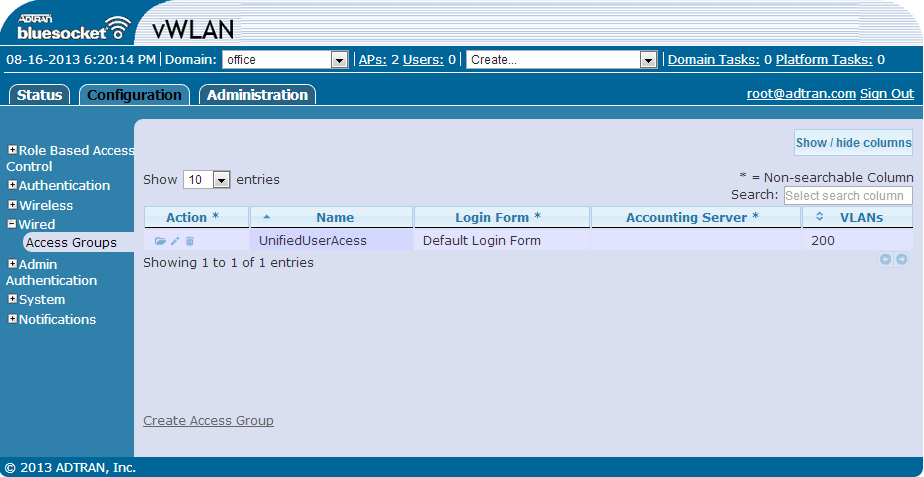 | 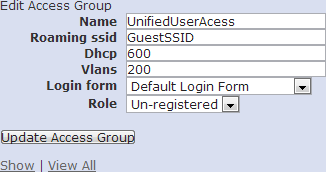 |
| Figure 8. vWLAN Wired Access Groups | Figure 9. vWLAN Wired Access Groups Configuration |
As seen in figure 9, there are six (6) options when configuring an Access Group.
- Name
- Roaming SSID
- DHCP
- Vlans
- Login form
- Role
The Name is used within the AP templates to identify the Access Group. This value must comply with RFC 952, and can be up to 32 characters long.
The Roaming SSID will allow wired clients to roam between a third-party access point and a BSAP without re-authenticating. The same SSID value must broadcast from both the third-party AP and the BSAP. This value is what allows wireless clients to have a seamless experience when roaming between third-party access points and BSAPs.
The DHCP value overrides the DHCP lease time configured on the network's DHCP server. The default value is 20 seconds, and a value of 0 disables the override. The override is useful in that can be used by administrators to force wired users back into the Un-registered role after a set period of time effectively forcing the wired clients to log out.
Vlans are a comma-separated list of untrusted VLANs to be used by the access group. There are three restrictions:
- an untrusted VLAN can only be a member of a single access group,
- an untrusted VLAN cannot overlap with a trusted location, and
- VLAN IDs 0 and 1 cannot be used.
The VLAN tags are used to determine which access group should be used. Multiple BSAPs cannot support the same untrusted VLAN, and therefore no two access groups can share the same untrusted VLANs. The example shown in figure 4 uses VLAN 200. This value corresponds to the AOS configuration shown below.
The Login Form is used when the wired clients start in the Un-registered role. This form is presented to the wired clients when they attempt to authenticate with vWLAN. The Role must be set to Un-registered if clients need to authenticate in any fashion. A default role other than Un-registered is allowed, however, wired clients will not be forced to login. Instead, they will be placed into the role specified, and the BSAP will enforce the appropriate policies. If the role is set to something other than Un-registered, an Accounting Server option will be presented.
The BSAPs must be configured to use the Access Group created above. The AP Templates configured under Configuration> Wireless> AP Templates will list the Access Groups configured on vWLAN (see figure 10). Add any Access Groups that BSAPs using this template should support. The vWLAN will determine which BSAP will support a given Access Group based on the active Locations reported by the BSAPs.
Figure 10. AP Template Access Groups Option
AOS Configuration Verification
The AOS configuration is verifiable through the GUI or CLI. The configuration can verified via the web GUI by navigating to Data> Switch> VLANs and Data> Switch> Ports which should produce similar screenshots to those shown in the AOS Configuration via the GUI section.
Verifying the AOS configuration via the CLI requires the use of various show commands entered at the enable prompt. The show vlans command will display all configured VLANs including port membership.
# show vlans
VLAN Name Status Type Media MTU
------------------------------------------------------------------
1 Default active static enet 1518
Membership Ports
------------------------------------------------------------
Configured giga-swx 1/0/33, giga-swx 1/0/34,
giga-swx 1/0/35, giga-swx 1/0/36,
giga-swx 1/0/37, giga-swx 1/0/38,
giga-swx 1/0/39, giga-swx 1/0/40,
giga-swx 1/0/41, giga-swx 1/0/42,
giga-swx 1/0/43, giga-swx 1/0/44,
giga-swx 1/0/45, giga-swx 1/0/46,
giga-swx 1/0/47, giga-swx 1/0/48
VLAN Name Status Type Media MTU
------------------------------------------------------------------
100 Wireless active static enet 1518
Membership Ports
------------------------------------------------------------
Configured giga-swx 1/0/33, giga-swx 1/0/48,
VLAN Name Status Type Media MTU
------------------------------------------------------------------
200 Wired Client VLAN active static enet 1518
Membership Ports
------------------------------------------------------------
Configured giga-swx 1/0/1, giga-swx 1/0/2,
giga-swx 1/0/3, giga-swx 1/0/4,
giga-swx 1/0/5, giga-swx 1/0/6,
giga-swx 1/0/7, giga-swx 1/0/8,
giga-swx 1/0/9, giga-swx 1/0/10,
giga-swx 1/0/11, giga-swx 1/0/12,
giga-swx 1/0/13, giga-swx 1/0/14,
giga-swx 1/0/15, giga-swx 1/0/16,
giga-swx 1/0/17, giga-swx 1/0/18,
giga-swx 1/0/19, giga-swx 1/0/20,
giga-swx 1/0/21, giga-swx 1/0/22,
giga-swx 1/0/23, giga-swx 1/0/24,
giga-swx 1/0/25, giga-swx 1/0/26,
giga-swx 1/0/27, giga-swx 1/0/28,
giga-swx 1/0/29, giga-swx 1/0/30,
giga-swx 1/0/31, giga-swx 1/0/32,
giga-swx 1/0/33
It is important to verify that the Wired Client VLAN is only active on ports used for wired clients and the BSAP servicing those clients. The Wired Client VLAN should not be configured on the Uplink port, and this is seen when looking at the VLAN 200 port membership. Similar information is shown when using the show interface status command. This will provide the physical state of each port as well as information regarding the switchport mode (access or trunk) of the port.
# show interface status
Port Name Status Vlan Duplex Speed Type
giga-swx 1/0/1 up 200 a-full a-100 Gig
giga-swx 1/0/2 up 200 a-full a-100 Gig
giga-swx 1/0/3 up 200 a-full a-100 Gig
giga-swx 1/0/4 up 200 a-full a-1G Gig
giga-swx 1/0/5 up 200 a-full a-100 Gig
giga-swx 1/0/6 up 200 a-full a-100 Gig
giga-swx 1/0/7 up 200 a-full a-100 Gig
giga-swx 1/0/8 up 200 a-full a-100 Gig
giga-swx 1/0/9 up 200 a-full a-100 Gig
giga-swx 1/0/10 up 200 a-full a-100 Gig
giga-swx 1/0/11 up 200 a-full a-1G Gig
giga-swx 1/0/12 up 200 a-full a-100 Gig
giga-swx 1/0/13 up 200 a-full a-1G Gig
giga-swx 1/0/14 up 200 a-full a-1G Gig
giga-swx 1/0/15 up 200 a-full a-100 Gig
giga-swx 1/0/16 up 200 a-full a-100 Gig
giga-swx 1/0/17 up 200 a-full a-100 Gig
giga-swx 1/0/18 up 200 a-full a-100 Gig
giga-swx 1/0/19 up 200 a-full a-100 Gig
giga-swx 1/0/20 up 200 a-full a-100 Gig
giga-swx 1/0/21 up 200 a-full a-100 Gig
giga-swx 1/0/22 up 200 a-full a-100 Gig
giga-swx 1/0/23 up 200 a-full a-100 Gig
giga-swx 1/0/24 up 200 a-full a-100 Gig
giga-swx 1/0/25 up 200 a-full a-100 Gig
giga-swx 1/0/26 up 200 a-full a-100 Gig
giga-swx 1/0/27 up 200 a-full a-100 Gig
giga-swx 1/0/28 up 200 a-full a-100 Gig
giga-swx 1/0/29 up 200 a-full a-100 Gig
giga-swx 1/0/30 up 200 a-full a-100 Gig
giga-swx 1/0/31 up 200 a-full a-100 Gig
giga-swx 1/0/32 up 200 a-full a-100 Gig
giga-swx 1/0/33 up trunk a-full a-1G Gig
giga-swx 1/0/34 up trunk a-full a-100 Gig
giga-swx 1/0/35 up trunk a-full a-100 Gig
giga-swx 1/0/36 up trunk a-full a-100 Gig
giga-swx 1/0/37 up trunk a-full a-100 Gig
giga-swx 1/0/38 up trunk a-full a-100 Gig
giga-swx 1/0/39 up trunk a-full a-100 Gig
giga-swx 1/0/40 up trunk a-full a-100 Gig
giga-swx 1/0/41 up trunk a-full a-100 Gig
giga-swx 1/0/42 up trunk a-full a-100 Gig
giga-swx 1/0/43 up trunk a-full a-100 Gig
giga-swx 1/0/44 up trunk a-full a-1G Gig
giga-swx 1/0/45 up trunk a-full a-100 Gig
giga-swx 1/0/46 up trunk a-full a-100 Gig
giga-swx 1/0/47 up trunk a-full a-100 Gig
giga-swx 1/0/48 up trunk a-full a-1G Gig
Access ports will simply list the VLAN ID while trunk ports will show "trunk" listed in the VLAN column. The individual port configurations can also be verified to ensure the correct VLANs are allowed across the 802.1q trunk. This is done using show running-config interface <chassis ID>/<slot>/<port>. The chassis ID is only required on AOS devices utilizing ActivChassis.
# show running-config interface gigabit-switchport 1/0/48
description Uplink
no shutdown
switchport mode trunk
switchport trunk allowed vlan 1-199,201-4094
The majority of troubleshooting in AOS will involve the use of the show commands above. These commands will aid in verifying the configuration of the AOS devices. It may be required to display the MAC address table using show mac address-table to confirm the wired clients are appearing on the proper ports.
# show mac address-table
Mac Address Table
------------------------------------------
Vlan Mac Address Type Ports
---- ----------- ---- -----
200 90:e6:ba:1b:29:17 DYNAMIC swx 0/16
Total Mac Addresses for this criterion: 1
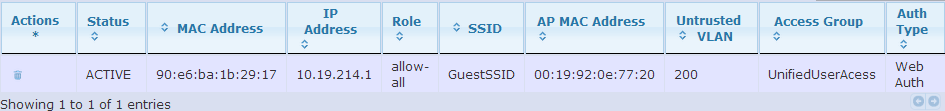
Troubleshooting from vWLAN may require the use of AP Traffic Captures. The capture type would need to be "wired" as all wired client traffic will flow into and out of the same Ethernet port on the BSAP. These captures will help gather information around areas such as ARP and DHCP which are necessary for the wired client to reach other network resources. Each user will also be displayed in the Status> Active Users table as shown in figure 11. The main fields to look for are IP Address, SSID, Untrusted VLAN, and Access Group.
Figure 11. Active Users Table
-
 Anonymous
Anonymous