- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Adtran Support Community
- :
- Discussion
- :
- NetVanta
- :
- NetVanta 3400 Series
- :
- Netvanta 3448 Remote Client VPN, assign a static IP to the remote client
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I have a Mobile Peer set up for a laptop that goes from one physical location to another. I am using Adtran Secure VPN Client to connect from the laptop to the Netvanta 3448's Mobile Peer. I set this up to work with no issue. The issue comes when I need this laptop to use the same IP address assigned by the Netvanta crypto ike pool (there are other clients that have to connect to this Mobile Peer). I have went to the Adtran adapter in network connections and gave the VPN adapter the static that I want it to be in a valid IP 10.5.12.1. When I do that the laptop wont connect to the Mobile Peer using the Adtran Secure VPN Client. I have also tried to assign the static IP address to the Profile on the Adtran VPN Client, this allowed me to connect to the Mobile Peer but the Laptop could no longer get the the applications that require it to show up as 10.5.12.1
I need the Mobile Peer to support multiple users (which it does) while allowing this one Laptop to have the static IP 10.5.12.1
Here is my Configuration:
crypto ike client configuration pool "VPN Client Users"
ip-range 10.5.12.1 10.5.12.254
dns-server 8.8.8.8 4.2.2.2
crypto ike policy 117
no initiate
respond anymode
local-id address 69.43.74.26
peer any
client configuration pool "VPN Client Users"
attribute 1
encryption 3des
hash md5
authentication pre-share
crypto ike remote-id any preshared-key N87*Nidid*l ike-policy 117 crypto map VPN 180 no-xauth
crypto map VPN 180 ipsec-ike
description VPN Client Users
match address VPN-180-vpn-selectors2
set transform-set esp-3des-esp-md5-hmac
ike-policy 117
mobile
ip access-list extended VPN-180-vpn-selectors2
permit ip 10.5.10.0 0.0.0.255 10.5.12.0 0.0.0.255
ip policy-class inside
allow list VPN-180-vpn-selectors2 stateless
nat source list web-acl-1 interface eth 0/1 overload
ip policy-class outside
allow reverse list VPN-180-vpn-selectors2 stateless
Please let me know what any of you think.
Thanks,
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Not the Solution
- Report Inappropriate Content
The Adtran Engineer solved this with ease. So thank you so much for your help Mark Fentz!
The fix was pretty simple and here it is:
crypto ike client configuration pool "VPN Client Users"
ip-range 10.5.12.5 10.5.12.254
dns-server 8.8.8.8 4.2.2.2
crypto ike remote-id fqdn test.com preshared-key N87*Nidid*l ike-policy 117 crypto map VPN 180 no-mode-config no-xauth
crypto ike remote-id any preshared-key N87*Nidid*l ike-policy 117 crypto map VPN 180 no-xauth
The "no-mode-config" tells the router not to assign it IP address. This allows the static IP. So in the Remote Client VPN software we set up its remote-id as "test.com" and it will pick up the first crypto ike and the router
will not give DHCP ip. You can use this same fqdn on all remote clients that need static.
The second crypo ike is same as orginal and works for all others from any ip with the proper settings and PSK.
Thanks,
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Accept as Solution
- Report Inappropriate Content
Re: Netvanta 3448 Remote Client VPN, assign a static IP to the remote client
It's been a long time since I've use the Adtran VPN client, but if the client supports using a static IP, you may be able to adjust your IP range in the ike client configuration pool.
ip-range 10.5.12.5 10.5.12.254
Then you could statically assign the client on the laptop any address between 10.5.12.1 - 10.5.12.4
This way you still have plenty of addresses for the other mobile users, but will will always know the IP of the laptop when it connects.
I know that will work with the Shew Soft VPN. I'm just not sure if static addresses are possible in the Adtran VPN client software. It most likely is an option.
R\
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Accept as Solution
- Report Inappropriate Content
Re: Netvanta 3448 Remote Client VPN, assign a static IP to the remote client
I will test this tomorrow and let you know how it goes. Today when I tested I did this, I assigned 10.5.12.1 to Laptop and the range on router was 10.5.12.1 - 10.5.12.254 but no other users was connected or attempted to connect. Like I said thank you for the idea and I will test it your way tomorrow and report back.
Thanks,
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Accept as Solution
- Report Inappropriate Content
Re: Netvanta 3448 Remote Client VPN, assign a static IP to the remote client
I have made these changes and tested. Here are the changes
crypto ike client configuration pool "VPN Client Users"
ip-range 10.5.12.5 10.5.12.254
dns-server 8.8.8.8 4.2.2.2
I went into my Laptop and Static assigned (On the Adtran Secure Client Virtual Local area connection) this IP address 10.5.12.1 /24 with the DNS 8.8.8.8 and 4.2.2.2 and I could connect to Adtran Secure VPN Client but not get to the things I should get to with my IP as 10.5.12.1. I then disconnected and set the Adtran Secure Client Virtual Local area connection to DHCP.
I switch the configuration back to:
crypto ike client configuration pool "VPN Client Users"
ip-range 10.5.12.1 10.5.12.254
dns-server 8.8.8.8 4.2.2.2
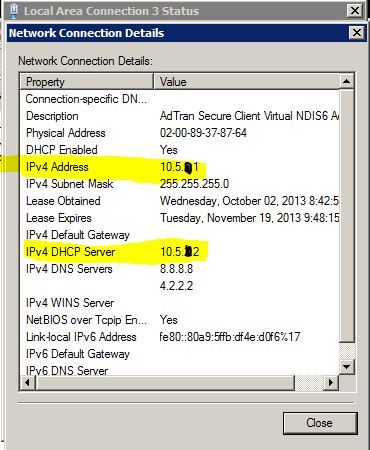
I Reconnect to Adtran Secure VPN Client and get IP 10.5.12.1 and I am able to get to applications that I should. I NOTICE one thing when I get DHCP IP address. I get an IPv$ DHCP Server address of 10.5.12.2 on my Adtran Secure Client Virtual Local area connection. There is no place to manually set this setting when you do it static.
I have inserted the DHCP image from Adtran Secure Client Virtual Local area connection.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Accept as Solution
- Report Inappropriate Content
Re: Netvanta 3448 Remote Client VPN, assign a static IP to the remote client
I tried configuring it in my ShrewSoft VPN client. It worked. I noticed that when I get a dhcp address, the subnet mask is 255.255.255.255 vs. 255.255.255.0. I set my static ip in the client that way and it worked. Can you give that a try and see how if that works for you?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Accept as Solution
- Report Inappropriate Content
Re: Netvanta 3448 Remote Client VPN, assign a static IP to the remote client
The Image I provide above is from a DHCP ip address that works. Adding a static IP address in with 255.255.255.255 would be outside of what happens with DHCP so I am thinking it wont work. I will try it anyway and report back. Thanks for help.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Accept as Solution
- Report Inappropriate Content
Re: Netvanta 3448 Remote Client VPN, assign a static IP to the remote client
I'm suggesting that you configure the router as follows:
crypto ike client configuration pool "VPN Client Users"
ip-range 10.5.12.5 10.5.12.254
dns-server 8.8.8.8 4.2.2.2
Then, in your VPN client assign 10.5.12.1 to the client statically with a subnet mask of 255.255.255.255.
I think it will work. I don't have a valid copy of the NetVanta VPN client to try it here on my bench. I know it works when I configure ShewSoft the same way.
I'm really curious to see if it works. Shrewsoft did not work when I set a static address and use 255.255.255.0.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Accept as Solution
- Report Inappropriate Content
Re: Netvanta 3448 Remote Client VPN, assign a static IP to the remote client
I just did exactly as you suggested and it does not work. It was a good try though. I am about to try using a Default gateway in my settings to see if that helps.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Accept as Solution
- Report Inappropriate Content
Re: Netvanta 3448 Remote Client VPN, assign a static IP to the remote client
Great. Well at least we know it will work with ShrewSoft. I'm interested to see how it turns out with the default gateway.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Accept as Solution
- Report Inappropriate Content
Re: Netvanta 3448 Remote Client VPN, assign a static IP to the remote client
It worked strange with a default gateway. If I leave VPN DHCP range 10.5.12.1-254 and use static IP with subnet mask 255.255.255.255 and default gateway 10.5.12.2 (which normally is assigned to DHCP server, I work fine. However this is not a solution because another user may connect first and take that IP address 10.5.12.1 and then the Laptop wont have access to the application/software that it needs.
What is ShrewSoft and how much does it cost?
Thanks,
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Accept as Solution
- Report Inappropriate Content
Re: Netvanta 3448 Remote Client VPN, assign a static IP to the remote client
I bet if you adjusted the range to exclude 12.1, it would still work.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Accept as Solution
- Report Inappropriate Content
Re: Netvanta 3448 Remote Client VPN, assign a static IP to the remote client
I did that too and it did not work. That is why I ask about ShrewSoft but I really want to make Adtran Secure VPN Client work because I have purchased 3 Lic for it already.
Thanks for all your help. I wish this was working.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Accept as Solution
- Report Inappropriate Content
Re: Netvanta 3448 Remote Client VPN, assign a static IP to the remote client
I have 5 licenses, but it is for an older version from maybe 6 years ago. It took them too long to get a client that worked with newer versions of Windows, so I was somewhat forced to use an alternate client.
ShrewSoft has two versions of their client, the free version which works great. They also have a licensed version that has some extended capabilities like split DNS. It does not connect automatically based on interesting traffic like Adtran’s VPN, but it does have auto-reconnect which is very nice.
It’s a little tricky getting the first one going, but after that you can export the configuration and then import it as a new one and modify user parameters.
It is not officially supported by Adtran, but Adtran does provide a guide for configuration.
https://supportforums.adtran.com/servlet/JiveServlet/downloadBody/2268-102-1-2397/Configuring%20the%20Shrew%20Soft%20VPN%20Client%20for%20AOS%20VPN.pdf
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Accept as Solution
- Report Inappropriate Content
Re: Netvanta 3448 Remote Client VPN, assign a static IP to the remote client
I can see two options to solve this issue.
- Anyone know how to do the Static IP on Remote Client VPN?
- Can I create two separate VPN Clients? (I dont think i can. Here is my router software: ADTRAN, Inc. OS version 18.03.01.00.E)
Anyone can help me out I would love it.
Thanks,
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Accept as Solution
- Report Inappropriate Content
Re: Netvanta 3448 Remote Client VPN, assign a static IP to the remote client
Have you tried setting up two different IP pools and two different ike policies? Then set up your laptop to connect on the 1st range and any other VPN client on the second range.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Accept as Solution
- Report Inappropriate Content
Re: Netvanta 3448 Remote Client VPN, assign a static IP to the remote client
I had tried this but I messed up the configuration. How to configure it?
Thanks,
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Accept as Solution
- Report Inappropriate Content
Re: Netvanta 3448 Remote Client VPN, assign a static IP to the remote client
You can create two different pools:
crypto ike client configuration pool "VPN Client Laptop"
ip-range 10.5.12.1 10.5.12.4
crypto ike client configuration pool "VPN Other Clients"
ip-range 10.5.12.5 10.5.12.254
Then set up two crypto ike policies, one for each pool.
Then two remote-ids one for the laptop and one for the other client(s).
Two crypto maps, for your two ike policies and finally set the firewall to allow the two IP ranges through.
Hope this helps.
--
Regards,
Mick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Accept as Solution
- Report Inappropriate Content
Re: Netvanta 3448 Remote Client VPN, assign a static IP to the remote client
Mick, I want to use your idea and have tried (unsuccessfully).
When you use a "Dynamically Addressed" or "Mobile Peer" the IKE Settings, IPSEC settings, and REMOTE ADDRESSING are all shared! You get a warning when creating the second Mobile Peer. If I create it the second Mobile Peer the first Mobile Peer no longer works. Any Suggestions?
Thank you for the help!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Accept as Solution
- Report Inappropriate Content
Re: Netvanta 3448 Remote Client VPN, assign a static IP to the remote client
Also this command makes an issue when doing Mobile Peer aka remote client
crypto ike remote-id any preshared-key N87*Nidid*l ike-policy 117 crypto map VPN 180 no-xauth
we use "remote-id any" so that when the laptops go from business to business and hotel to hotel it will always work.
I don't see a way to set up to make another Remote Client work without breaking the first one.
So my thoughts are figure out how to assign static IP to two of the Remote Clients and let the rest do DHCP.
Thanks,
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Accept as Solution
- Report Inappropriate Content
Re: Netvanta 3448 Remote Client VPN, assign a static IP to the remote client
So sorry, I misunderstood your original requirement! Only one remote-id any is available. Other peers will have to be static rather than mobile. I don't know if there is a workaround on this problem. Hopefully someone from Adtran will pop in with a response, or you can raise a support ticket.
--
Regards,
Mick