- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Adtran Support Community
- :
- Discussion
- :
- Total Access
- :
- Total Access 900/900e Series
- :
- How to provide router behind 924e 3rd gen with Public IP's for routing to server and LAN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How to provide router behind 924e 3rd gen with Public IP's for routing to server and LAN
Hi,
I've got 4 bonded T1's terminating in a 924e 3rd Gen (R11.10.0.E) with 8 analog lines also terminating in the TA.
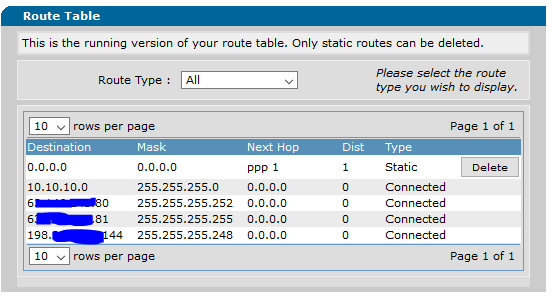
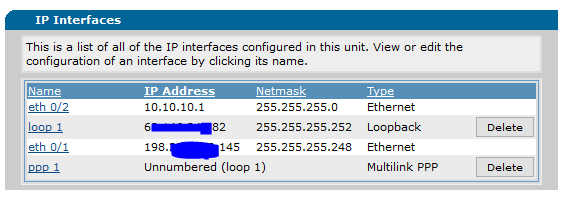
WAN Serial: 6x.xx.xxx.81/30 (255.255.255.252)
Customer Serial: 6x.xx.xxx.82/30 (255.255.255.252)
LAN IP Block: 198.xxx.xxx.144/29 (255.255.255.248)
Right now, 198.xxx.xxx.145 is assigned to eth 0/1, to which I've connected my LAN. From there, I can assign my internal router a public IP address of .146, .147, .148, etc... or I can insert a dumb switch, and have any connected assets pull those IP's. The problem is that I want a firewall in between, I don't want to connect the assets direct to those public facing IP's.
What I'm trying to do:
I need to provide a public IP address to my server. My hardware tech support for my internal firewall/router has advised that I place the 924e in bridge mode, so as to terminate the xxx.82/30 to my internal router, and have that router then assign the 145/29 block to separate VLANs (such that .146/29 goes to SERVER A, .147.29 goes to SERVER B, etc).
As near as I can tell, the 924e doesn't really support BRIDGE MODE (or at least, not without breaking the voice services). I tried following the directions to set the PPP multilink (WAN) + eth 0/1 (LAN) to "no IP address", place them both in BVI bridge group "1", and assigning an IP to BVI 1, then connecting my router to accept .82/30 as a WAN connection from the BVI on eth 0/1, but I was just guessing at the settings and couldn't get it to work (what should the default gateway be on the TA be? what ip should the BVI group be? in my internal router, what do i set as the gateway for the .82/30 IP assignment? I deleted the loop 1, but that seemed to just break everything - do I need loop 1, and if so, how should it be configured?).
Even if Bridge mode isn't the answer - is there a way to do this without resorting to the dumb switch mentioned above? Also note that when I'm trying to set up Direct Access on my windows 2012 r2 essentials server, I'm trying to use multi-homed (2 nics, one facing a public IP and the other facing internal lan on different subnet) - and the NIC for the public side REQUIRES a public IP address, so I can't 1:1 NAT it in on a local IP...which is what is causing all this headache to begin with.
Probably important to note that these are ANALOG lines going into the 924e, which then go to a 60 block off the FXS port thing. Those then feed an analog card in my server which is managed by a virtual machine/soft PBX, which connects to IP phones. So calls are routed from analog - > PBX - > IP phones, and I don't manage SIP trunks or anything of the like inside the TA. In fact, I don't really know how the TA is involved in the voice end of things, since they gave me those 8 phone plugs for my analog card, and I set up my whole system inside my soft PBX - never once logged into the TA until now. Point is, I'm not sure if / what modifications to the TA WAN/LAN config will impact the phones (if at all?).
I've attached two pictures - the routing table of the GUI and the IP interface of the GUI. I've also attached the config. Any help you can provide would be much appreciated!
!
! ADTRAN, Inc. OS version R11.10.0.E
! Boot ROM version R10.9.3.B1
! Platform: Total Access 900e (3rd Gen), part number [xyz]
! Serial number [xyz]
!
hostname "[xyz]"
enable password md5 encrypted [xyz]
!
clock timezone -5-Eastern-Time
!
ip subnet-zero
ip classless
ip routing
ipv6 unicast-routing
!
domain-proxy
!
no auto-config
auto-config authname [xyz] encrypted password [xyz]
!
event-history on
no logging forwarding
no logging console
no logging email
!
service password-encryption
!
username "[xyz]" password encrypted "[xyz]"
username "[xyz]" password encrypted "[xyz]"
username "[xyz]" password encrypted "[xyz]"
username "[xyz]" password encrypted "[xyz]"
!
ip firewall
no ip firewall alg msn
no ip firewall alg mszone
no ip firewall alg h323
!
no dot11ap access-point-control
!
qos map SIP 10
match precedence 5
priority percent 90
qos map SIP 20
match precedence 3
bandwidth percent 5
!
qos map RESETIPPREC 10
match precedence 1
match precedence 2
match precedence 3
match precedence 4
match precedence 5
match precedence 6
match precedence 7
set precedence 0
!
interface loop 1
ip address 6x.xxx.xxx.82 255.255.255.252
no shutdown
!
interface eth 0/1
ip address 198.xxx.xxx.145 255.255.255.248
ip access-policy DATA-LAN
qos-policy in RESETIPPREC
no shutdown
!
!
interface eth 0/2
description LOCAL management
ip address 10.10.10.1 255.255.255.0
ip mtu 1500
no shutdown
!
!
!
interface gigabit-eth 0/1
no ip address
shutdown
!
!
!
!
interface t1 0/1
description [xyz]
tdm-group 1 timeslots 1-24 speed 64
no shutdown
!
interface t1 0/2
description [xyz]
tdm-group 1 timeslots 1-24 speed 64
no shutdown
!
interface t1 0/3
description [xyz]
tdm-group 1 timeslots 1-24 speed 64
no shutdown
!
interface t1 0/4
description [xyz]
tdm-group 1 timeslots 1-24 speed 64
no shutdown
!
!
interface fxs 0/1
no shutdown
!
interface fxs 0/2
no shutdown
!
interface fxs 0/3
no shutdown
!
interface fxs 0/4
no shutdown
!
interface fxs 0/5
no shutdown
!
interface fxs 0/6
no shutdown
!
interface fxs 0/7
no shutdown
!
interface fxs 0/8
no shutdown
!
interface fxs 0/9
no shutdown
!
interface fxs 0/10
no shutdown
!
interface fxs 0/11
no shutdown
!
interface fxs 0/12
no shutdown
!
interface fxs 0/13
no shutdown
!
interface fxs 0/14
no shutdown
!
interface fxs 0/15
no shutdown
!
interface fxs 0/16
no shutdown
!
interface fxs 0/17
no shutdown
!
interface fxs 0/18
no shutdown
!
interface fxs 0/19
no shutdown
!
interface fxs 0/20
no shutdown
!
interface fxs 0/21
no shutdown
!
interface fxs 0/22
no shutdown
!
interface fxs 0/23
no shutdown
!
interface fxs 0/24
no shutdown
!
!
interface fxo 0/0
no shutdown
!
interface ppp 1
description [xyz]
ip unnumbered loop 1
ip access-policy SIP-FIREWALL
media-gateway ip primary
ppp multilink
max-reserved-bandwidth 100
qos-policy out SIP
acfc accept-compressed
no lldp send-and-receive
no shutdown
cross-connect 1 t1 0/1 1 ppp 1
cross-connect 2 t1 0/2 1 ppp 1
cross-connect 3 t1 0/3 1 ppp 1
cross-connect 4 t1 0/4 1 ppp 1
!
timing-source t1 0/1
!
ip access-list standard [xyz ADMIN]
permit [xyz]
permit [xyz]
permit [xyz]
permit [xyz]
permit [xyz]
permit [xyz]
permit [xyz]
permit [xyz]
permit [xyz]
permit [xyz]
permit [xyz]
permit host 6x.xxx.xxx.81
!
ip access-list extended DATA-SUBNET
permit ip 198.xxx.xxx.144 0.0.0.7 any
!
ip access-list extended INTERNET
permit ip any 198.xxx.xxx.144 0.0.0.7
!
ip access-list extended SIP
permit udp 6x.xxx.xxx.0 0.0.0.255 any eq 5060
!
ip policy-class DATA-LAN
allow list DATA-SUBNET self
allow list DATA-SUBNET
!
ip policy-class SIP-FIREWALL
allow list [xyz ADMIN] self
allow list SIP self
allow list INTERNET
!
ip route 0.0.0.0 0.0.0.0 ppp 1
!
no tftp server
no tftp server overwrite
http server
http secure-server 8081
snmp agent
ip ftp server
no ip scp server
no ip sntp server
!
ip ftp access-class [xyz] ADMIN in
http ip secure-access-class [xyz] ADMIN in
!
snmp-server management-url "[xyz]"
snmp-server management-url-label "[xyz]"
snmp-server location "[xyz]"
!
sip
sip udp 5060
no sip tcp
no sip tls
!
voice transfer unattended
!
voice feature-mode network
voice forward-mode network
!
voice spre 1 *XX&
!
voice dial-plan 1 local NXX-NXX-XXXX
voice dial-plan 2 long-distance 1-NXX-NXX-XXXX
voice dial-plan 3 international 011$
voice dial-plan 4 operator-assisted 0$
!
voice codec-list G711
codec g711ulaw
!
voice trunk T01 type sip
description "SIP Link"
sip-server primary 6x.xxx.xxx.205
registrar primary 6x.xxx.xxx.205
outbound-proxy primary 6x.xxx.xxx.203
conferencing-uri "conf"
domain [xyz]
register [xyz] auth-name "[xyz]" password encrypted "[xyz]"
register [xyz] auth-name "[xyz]" password encrypted "[xyz]"
register [xyz] auth-name "[xyz]" password encrypted "[xyz]"
register [xyz] auth-name "[xyz]" password encrypted "[xyz]"
register [xyz] auth-name "[xyz]" password encrypted "[xyz]"
register [xyz] auth-name "[xyz]" password encrypted "[xyz]"
register [xyz] auth-name "[xyz]" password encrypted "[xyz]"
codec-list G711 both
!
voice grouped-trunk SIP
trunk T01
accept $ cost 0
!
voice user [xyz]
connect fxs 0/2
no cos
password encrypted "[xyz]"
no call-waiting
caller-id-override external-number [xyz]
sip-authentication password encrypted "[xyz]"
modem-passthrough
!
voice user [xyz]
connect fxs 0/3
no cos
password encrypted "[xyz]"
no call-waiting
caller-id-override external-number [xyz]
sip-authentication password encrypted "[xyz]"
modem-passthrough
!
voice user [xyz]
connect fxs 0/4
no cos
password encrypted "[xyz]"
no call-waiting
caller-id-override external-number [xyz]
sip-authentication password encrypted "[xyz]"
modem-passthrough
!
voice user [xyz]
connect fxs 0/5
no cos
password encrypted "[xyz]"
no call-waiting
caller-id-override external-number [xyz]
sip-authentication password encrypted "[xyz]"
modem-passthrough
!
voice user [xyz]
connect fxs 0/6
no cos
password encrypted "[xyz]"
no call-waiting
caller-id-override external-number [xyz]
sip-authentication password encrypted "[xyz]"
modem-passthrough
!
voice user [xyz]
connect fxs 0/7
no cos
password encrypted "[xyz]"
no call-waiting
caller-id-override external-number [xyz]
sip-authentication password encrypted "[xyz]"
modem-passthrough
!
voice user [xyz]
connect fxs 0/1
no cos
password encrypted "[xyz]"
no call-waiting
caller-id-override external-number [xyz]
sip-authentication password encrypted "[xyz]"
modem-passthrough
!
line con 0
login local-userlist
!
line telnet 0 4
login local-userlist
no shutdown
ip access-class [xyz] ADMIN in
line ssh 0 4
login local-userlist
no shutdown
ip access-class [xyz] ADMIN in
!
sntp server 204.xxx.xx.2
!
end
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Accept as Solution
- Report Inappropriate Content
Re: How to provide router behind 924e 3rd gen with Public IP's for routing to server and LAN
Allan, without a second public subnet to work with in between the 924 and the firewall, you wouldn't be able to pass that subnet along to the LAN port of the firewall. You could do a private subnet and NAT on the 924, but double NAT can cause additional problems. One possible option would just be to enable 802.1q on the 924 and do your VLANs from there. You could then hand out public IPs directly to some devices while providing private IPs to others.
Thanks
Jay
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Accept as Solution
- Report Inappropriate Content
Re: How to provide router behind 924e 3rd gen with Public IP's for routing to server and LAN
I went ahead and flagged this post as "Assumed Answered". If any of the responses on this thread assisted you, please mark them as Correct or Helpful as the case may be with the applicable buttons. This will make them visible and help other members of the community find solutions more easily. If you still need assistance, we would be more than happy to continue working with you on this - just let us know in a reply.
Thanks,
Jay
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Accept as Solution
- Report Inappropriate Content
Re: How to provide router behind 924e 3rd gen with Public IP's for routing to server and LAN
Even if bridging would work, I don't see what advantage it would offer you. Your /30 is the WAN network for your IAD; Loopback 1 is actually the IADs WAN network as specified by the "ip unnumbered loopback 1" command under PPP settings. .80 is the network, .81 is probably the WAN gateway, and .82 is the IP on your IAD.
If your Windows server requires a direct public IP, then chances are you should be configuring Windows firewall (or some sort of security filter to protect from public intrusion) on it. Plus, your IAD already has firewall service enabled on it with rules allowing ALL traffic through to the LAN IPs. You could make this more restrictive if you desired, like limiting traffic to a specific IP only over HTTP/HTTPS. And if you are doing that, you shouldn't need to put an additional firewall in front of it. So what is the issue with putting a 5 port dumb switch off the eth0/1 port and plugging one port into your LAN firewall and another into the Win2012 server? That would be a pretty standard way of utilizing a /29 public IP block from a single Ethernet port from a service provider.